
NESSUS

Download the full report here:
https://hickszilla.com/wp-content/uploads/2023/06/Utilizing-NESSUS-for-Vulnerability-Scanning-in-Cybersecurity-1.pdf

Cyber Security Foundational Knowledge: NESSUS Vulnerability Scanning
Date: 24 June 2023
1. Introduction
2. Vulnerability Scanning Overview
3. NESSUS: An Overview
4. Importance of NESSUS in Cybersecurity
5. Benefits and Challenges of Using NESSUS
6. Best Practices for Effective Vulnerability Management using NESSUS
7. Case Studies and Success Stories
8. Future Developments and Trends
9. Vulnerability Scanning Walkthrough
10. Conclusion
1. Introduction
Vulnerability scanning is a vital component of cybersecurity, helping organizations identify and address potential weaknesses in their systems and networks. NESSUS, a leading vulnerability scanning tool, offers powerful features and capabilities for this purpose. By conducting regular scans with NESSUS, organizations can proactively manage their risks, prioritize vulnerabilities, and enhance their security posture. This article provides an overview of vulnerability scanning, highlights the significance of NESSUS, discusses its benefits and challenges, and offers best practices for effective vulnerability management.
2. Vulnerability Scanning Overview
Vulnerability scanning is the automated process of identifying and assessing security vulnerabilities in software, systems, and networks. It involves using specialized tools to scan and analyze various components for weaknesses that could be exploited by attackers.
The objectives of vulnerability scanning are twofold. First, it aims to identify potential vulnerabilities in order to prevent potential security breaches. By regularly scanning systems and networks, organizations can stay ahead of potential threats and take timely actions to remediate vulnerabilities. Second, vulnerability scanning helps prioritize vulnerabilities based on their severity and potential impact, enabling organizations to allocate resources effectively for remediation efforts.
Vulnerability scanning offers several benefits to organizations. Firstly, it enables proactive risk management by identifying vulnerabilities before they can be exploited by malicious actors. This helps prevent data breaches, service disruptions, and financial losses. Secondly, vulnerability scanning assists in meeting compliance and regulatory requirements. By identifying and addressing vulnerabilities, organizations can ensure adherence to security standards and frameworks. Additionally, vulnerability scanning enhances the overall security posture of an organization by providing insights into potential entry points for cyber threats and allowing for timely remediation.
In vulnerability management processes, vulnerability scanning plays a crucial role. It serves as the initial step in the vulnerability management lifecycle, providing organizations with a comprehensive view of their security vulnerabilities. Vulnerability scanning helps organizations identify and prioritize vulnerabilities, allowing them to allocate resources effectively for remediation efforts. It also supports ongoing monitoring and assessment of the security posture, enabling organizations to continuously identify and address emerging vulnerabilities.
Overall, vulnerability scanning is a fundamental practice in cybersecurity, contributing to the proactive identification and remediation of vulnerabilities. It plays a vital role in vulnerability management processes, enabling organizations to prioritize and mitigate risks effectively, enhance their security posture, and ensure compliance with industry standards and regulations.
3. NESSUS: An Overview
NESSUS is a widely recognized and powerful vulnerability scanning tool that aids in identifying and addressing security vulnerabilities in software, systems, and networks. It offers a comprehensive set of features and capabilities that make it an essential tool for organizations in their cybersecurity efforts.
The history of NESSUS traces back to 1998 when Renaud Deraison developed it as an open-source project. Over the years, NESSUS has evolved and gained popularity due to its effectiveness and reliability. In 2005, Tenable Network Security, a cybersecurity company, acquired NESSUS and continued its development, enhancing its capabilities and expanding its user base.
NESSUS boasts an extensive range of features and capabilities that contribute to its effectiveness as a vulnerability scanning tool. It employs a vast vulnerability knowledge base, constantly updated with the latest security vulnerabilities and threats, to provide accurate and up-to-date scanning results. NESSUS supports both active and passive scanning techniques, allowing organizations to comprehensively analyze their systems and networks for vulnerabilities.
The tool offers various scanning options, including authenticated scans that provide deeper insights into the security posture by accessing the target systems with proper credentials. NESSUS can scan multiple operating systems, network devices, and applications, making it versatile for diverse environments.
NESSUS also provides flexible deployment options. It can be deployed as an on-premises solution, allowing organizations to have full control over their scanning processes and data. Additionally, cloud-based deployment options are available, enabling organizations to leverage the scalability and convenience of the cloud for vulnerability scanning.
The architecture of NESSUS consists of a distributed framework. It comprises multiple components, such as the NESSUS scanner, which performs the actual scanning, and the NESSUS server, which manages and coordinates scanning activities. This distributed architecture allows for scalability and efficient scanning across large and complex environments.
In summary, NESSUS is an industry-leading vulnerability scanning tool with a rich history and development track record. Its features and capabilities, along with its flexible architecture and deployment options, make it a valuable asset for organizations seeking to identify and address vulnerabilities in their systems and networks.
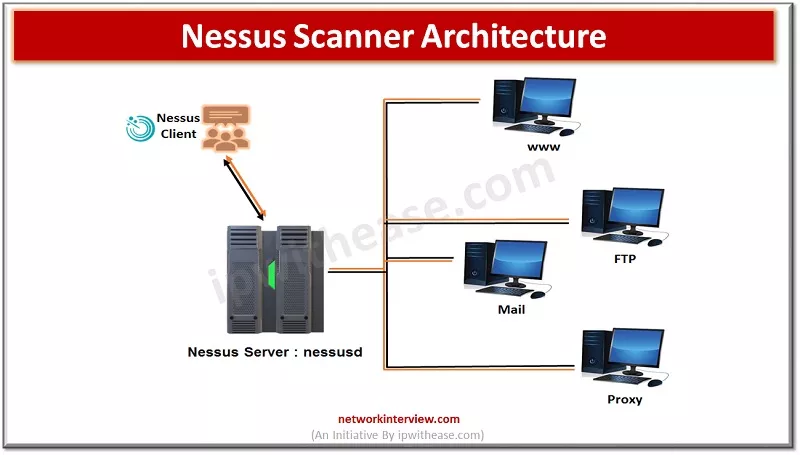
4. Importance of NESSUS in Cybersecurity
Identification and assessment of vulnerabilities involve a systematic process to identify potential weaknesses in a system or network. This includes performing regular vulnerability assessments and penetration testing, scanning the system or network for known vulnerabilities, analyzing system logs and monitoring network traffic for suspicious activities, conducting code reviews and security audits, and implementing intrusion detection and prevention systems.
Detection of common security misconfigurations is crucial to maintaining a secure environment. This involves regularly reviewing and updating security configurations, implementing secure default settings for systems and applications, scanning systems and networks for misconfigurations, conducting vulnerability assessments and penetration tests to identify misconfigured settings, and using automated tools to detect common security misconfigurations.
Compliance and regulatory considerations play a vital role in maintaining security. It involves understanding and complying with applicable regulations and industry standards, as well as implementing security controls and measures to meet compliance requirements.
Integration with other security tools and frameworks is essential for a comprehensive security approach. This includes integrating with security information and event management (SIEM) systems for centralized log analysis and correlation, leveraging threat intelligence platforms to enhance threat detection and response capabilities, integrating with identity and access management (IAM) solutions for robust authentication and authorization, connecting with vulnerability management tools to streamline the remediation process, and integrating with incident response platforms for efficient incident handling and investigation.
5. Benefits and Challenges of Using NESSUS
Planning and scoping vulnerability scans involve strategically determining the scope and objectives of the scans. This includes defining which systems, networks, and assets will be included in the assessment. The goals of the scans, such as compliance requirements or risk mitigation, are identified. A schedule is established to ensure regular scans are conducted. The scanning methodology, whether it is authenticated or unauthenticated, is determined. Potential impact on production systems is carefully considered, and measures are taken to minimize disruptions.
Configuring and optimizing NESSUS scans requires fine-tuning the scan settings to achieve accurate and comprehensive vulnerability detection. Scan policies are created based on specific requirements and compliance standards. Custom configurations are implemented to include or exclude specific vulnerability checks as needed. Scan intensity levels are adjusted to suit the target systems and network environment. Scan schedules and frequency are set to align with organizational needs. Performance optimization techniques, such as parallel scanning, distributed scanning, or agent-based scanning, are employed to improve efficiency.
Prioritizing and remediating vulnerabilities is a critical process to address the most significant risks in a timely manner. The severity and impact of vulnerabilities are analyzed using factors like CVSS scores, exploitability, and potential business impact. A vulnerability prioritization framework or matrix is established to guide decision-making. Resources and timelines are allocated for vulnerability remediation based on prioritization. Temporary mitigations or workarounds are implemented for high-risk vulnerabilities while permanent fixes are being developed. Progress tracking mechanisms ensure that identified vulnerabilities are promptly addressed and closed.
Integrating vulnerability scanning into the security workflow involves incorporating it as an integral component of the overall security operations. This may include integrating NESSUS scans with other security tools and frameworks such as security information and event management (SIEM) systems for centralized log analysis and correlation. The integration enables streamlined incident response and enhanced threat detection capabilities. By seamlessly integrating vulnerability scanning into the security workflow, organizations can improve their overall security posture and effectively manage risks.
6. Best Practices for Effective Vulnerability Management using NESSUS
Planning and scoping vulnerability scans involve strategically determining the scope and objectives of the scans. This includes defining which systems, networks, and assets will be included in the assessment. The goals of the scans, such as compliance requirements or risk mitigation, are identified. A schedule is established to ensure regular scans are conducted. The scanning methodology, whether it is authenticated or unauthenticated, is determined. Potential impact on production systems is carefully considered, and measures are taken to minimize disruptions.
Configuring and optimizing NESSUS scans requires fine-tuning the scan settings to achieve accurate and comprehensive vulnerability detection. Scan policies are created based on specific requirements and compliance standards. Custom configurations are implemented to include or exclude specific vulnerability checks as needed. Scan intensity levels are adjusted to suit the target systems and network environment. Scan schedules and frequency are set to align with organizational needs. Performance optimization techniques, such as parallel scanning, distributed scanning, or agent-based scanning, are employed to improve efficiency.
Prioritizing and remediating vulnerabilities is a critical process to address the most significant risks in a timely manner. The severity and impact of vulnerabilities are analyzed using factors like CVSS scores, exploitability, and potential business impact. A vulnerability prioritization framework or matrix is established to guide decision-making. Resources and timelines are allocated for vulnerability remediation based on prioritization. Temporary mitigations or workarounds are implemented for high-risk vulnerabilities while permanent fixes are being developed. Progress tracking mechanisms ensure that identified vulnerabilities are promptly addressed and closed.
Integrating vulnerability scanning into the security workflow involves incorporating it as an integral component of the overall security operations. This may include integrating NESSUS scans with other security tools and frameworks such as security information and event management (SIEM) systems for centralized log analysis and correlation. The integration enables streamlined incident response and enhanced threat detection capabilities. By seamlessly integrating vulnerability scanning into the security workflow, organizations can improve their overall security posture and effectively manage risks.
7. Case Studies and Success Stories
NESSUS has proven to be beneficial to numerous organizations in enhancing their security posture and reducing risks. The following explores real world exampls of organizations that have benefited from NESSUS and the impact it has had on their security.
Financial institutions, such as banks, have leveraged NESSUS to conduct regular network scans. By identifying vulnerabilities within their infrastructure, these organizations can effectively mitigate the risk of data breaches and unauthorized access to sensitive financial information. This proactive approach ensures that their systems remain secure and their customers' data protected.
Government agencies, at various levels, have also embraced NESSUS to assess the security of their networks and systems. Through comprehensive scanning, NESSUS helps these agencies identify vulnerabilities and implement necessary patches and security measures. This diligent approach strengthens their overall security posture and safeguards critical government assets from cyber threats.
In the healthcare industry, NESSUS plays a crucial role in helping providers maintain the security of their networks, medical devices, and software systems. Given the sensitivity of patient data, healthcare organizations rely on NESSUS to identify vulnerabilities and promptly address them. By doing so, they ensure the protection of patient information, regulatory compliance, and the integrity of their systems.
Technology companies, including software development firms and IT service providers, have integrated NESSUS into their security practices. By scanning their software applications, network infrastructure, and cloud environments, these organizations can identify vulnerabilities early in the development and deployment stages. This proactive approach enables them to rectify issues before products or services reach customers, thus minimizing security incidents and strengthening customer trust.
Educational institutions, such as colleges and universities, also benefit from NESSUS. By conducting thorough scans of their IT infrastructure, including servers, databases, and educational systems, these institutions can identify vulnerabilities that could compromise sensitive research, student data, and faculty information. NESSUS helps them maintain a secure learning environment and protect valuable assets.
The impact of NESSUS on security posture and risk reduction is evident through various factors. It helps organizations identify known vulnerabilities, ensuring they are promptly addressed. NESSUS also assists in patch management by highlighting missing patches and outdated software versions, reducing the risk of exploitation. Additionally, it conducts configuration assessments, enabling organizations to identify and rectify misconfigurations that may serve as potential entry points for attackers. Through vulnerability prioritization and remediation guidance, NESSUS aids in reducing overall risk exposure by addressing critical vulnerabilities first and implementing appropriate security controls.
NESSUS demonstrates its evolving capabilities and enhancements that actively contribute to organizations' security posture and risk reduction. The tool continuously adapts to the ever-changing threat landscape and incorporates advanced features to stay ahead of emerging vulnerabilities.
Through seamless integration with emerging technologies and frameworks, NESSUS enables organizations to effectively safeguard their digital assets. It actively supports the integration with cloud platforms, IoT devices, and containerization technologies, allowing comprehensive vulnerability assessment across diverse environments. By embracing these advancements, organizations can ensure that their security measures remain robust and adaptable to new challenges.
While NESSUS offers significant benefits, there are potential challenges and future directions to consider. As cyber threats become more sophisticated, the tool needs to stay updated with the latest attack vectors and vulnerability types. Continuous research and development efforts are necessary to enhance NESSUS's detection capabilities and ensure its effectiveness in identifying zero-day vulnerabilities and advanced persistent threats.
The tool should also align with evolving compliance requirements and industry standards. It should actively support frameworks such as the Payment Card Industry Data Security Standard (PCI DSS) and the National Institute of Standards and Technology (NIST) guidelines, enabling organizations to meet regulatory obligations effectively.
NESSUS has the potential to further enhance automation and integration capabilities. By leveraging artificial intelligence and machine learning algorithms, the tool can streamline vulnerability management processes, prioritize remediation efforts, and provide more accurate risk assessments. Integration with security orchestration, automation, and response (SOAR) platforms would enable seamless collaboration between NESSUS and other security tools, optimizing incident response and threat mitigation.
To maximize the benefits of NESSUS, organizations should invest in comprehensive training and skill development programs. This would ensure that security teams possess the necessary expertise to leverage the tool's advanced functionalities effectively. Additionally, organizations should establish robust communication channels with NESSUS's development team, providing feedback and suggestions to drive continuous improvement and address evolving security needs.
NESSUS's active role in enhancing security posture and risk reduction is evident through its evolving capabilities, integration with emerging technologies, and its potential for future advancements. By embracing NESSUS and its continuous enhancements, organizations can effectively mitigate vulnerabilities, proactively protect their assets, and stay resilient against evolving cyber threats.
When logging into the NESSUS platform, the security analyst is presented with a comprehensive dashboard that offers a high-level overview of the vulnerability scanning process. The analyst starts by configuring the scan parameters, defining the target assets, and selecting the desired scan type.
NESSUS scan templates are predefined configurations used to conduct vulnerability scans. Examples include Basic Network Scan for network infrastructure and Web Application Scan for web applications. These templates streamline the scanning process by providing specific settings for different types of scans.
With the parameters set, the analyst initiates the vulnerability scan, which triggers NESSUS to systematically probe the target assets for potential vulnerabilities. The tool actively scans networks, systems, and applications, utilizing a vast database of known vulnerabilities and attack patterns.
As NESSUS conducts the scan, it meticulously examines each asset, performing vulnerability checks and identifying any weaknesses or misconfigurations. The active scanning process involves sending specific packets to target systems, emulating potential attack scenarios to identify vulnerabilities that could be exploited by malicious actors.
Upon completion of the scan, NESSUS generates a detailed report that provides a comprehensive overview of the vulnerabilities detected. The report includes information such as the severity of each vulnerability, affected assets, potential impact, and recommended remediation steps.
8. Future Developments and Trends
9. Vulnerability Scanning Walkthrough
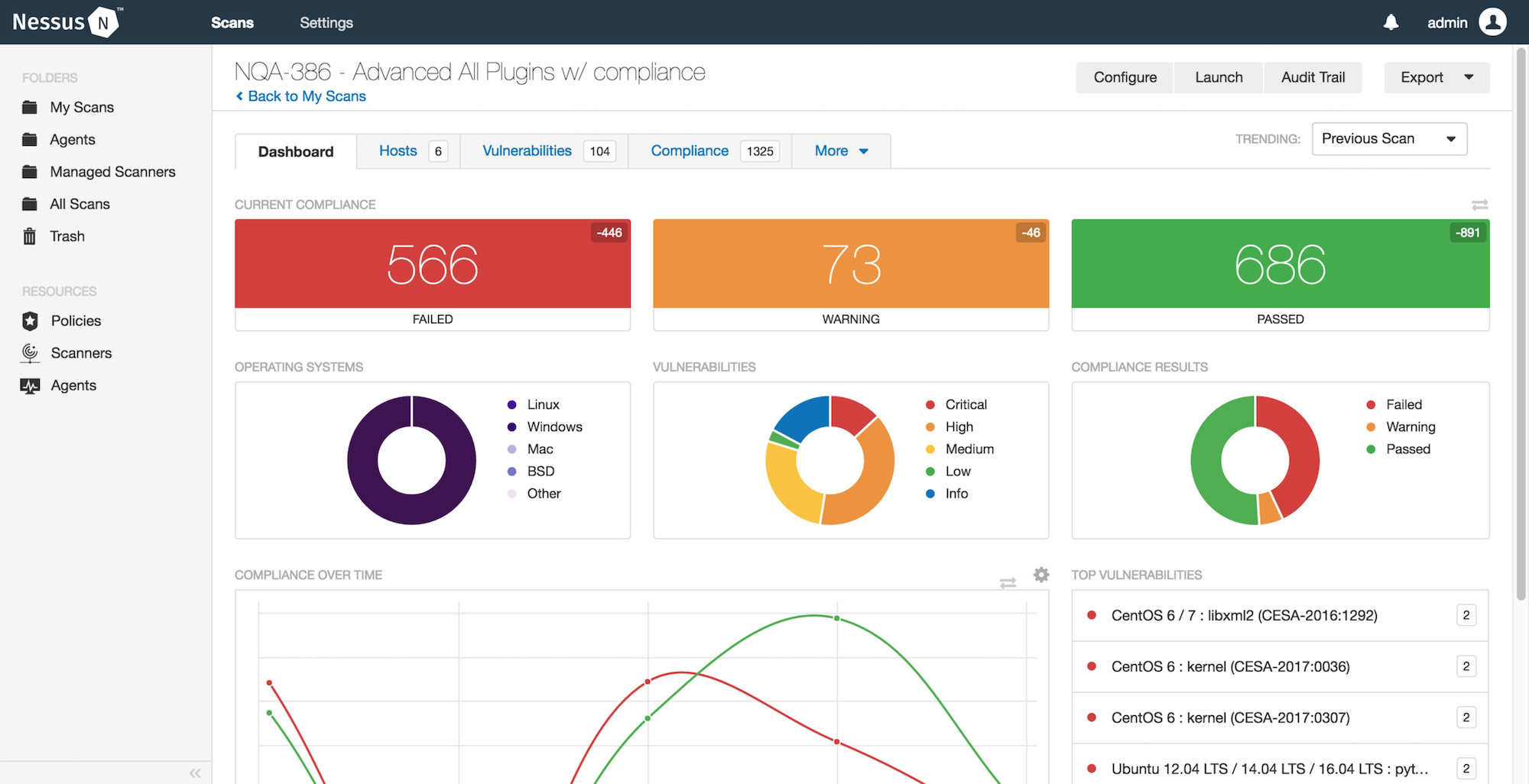
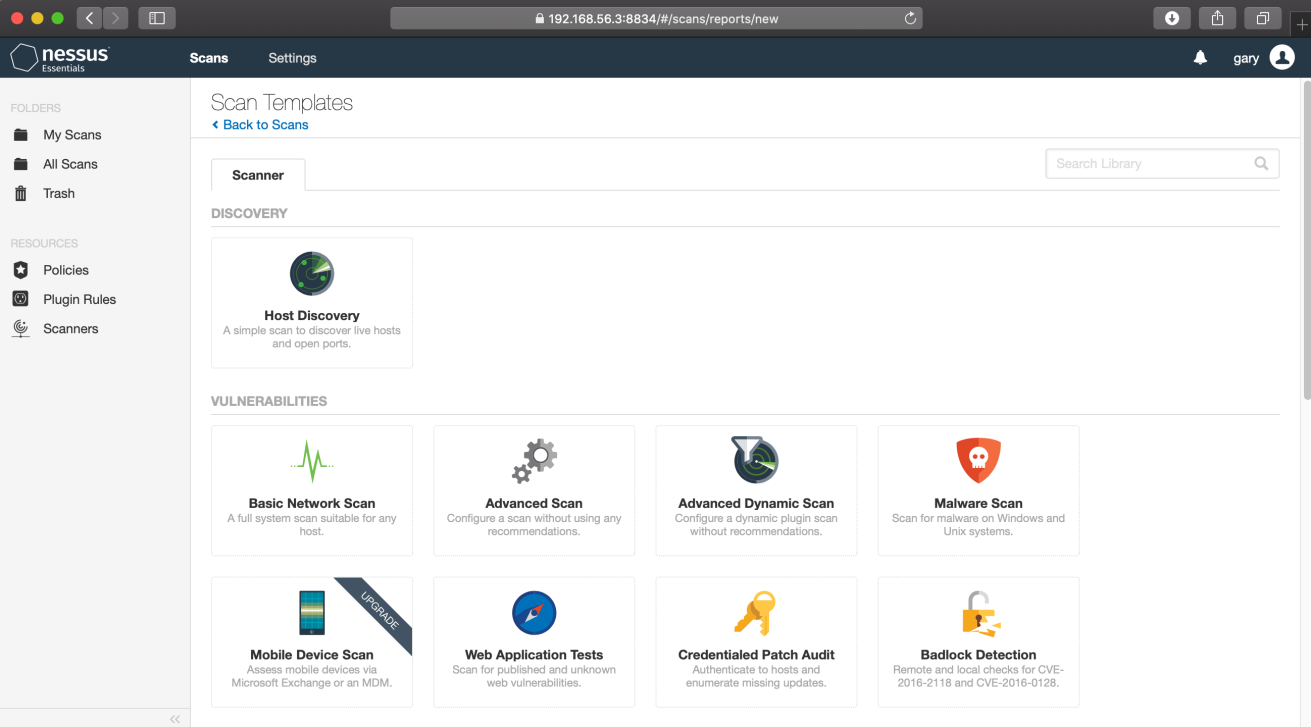
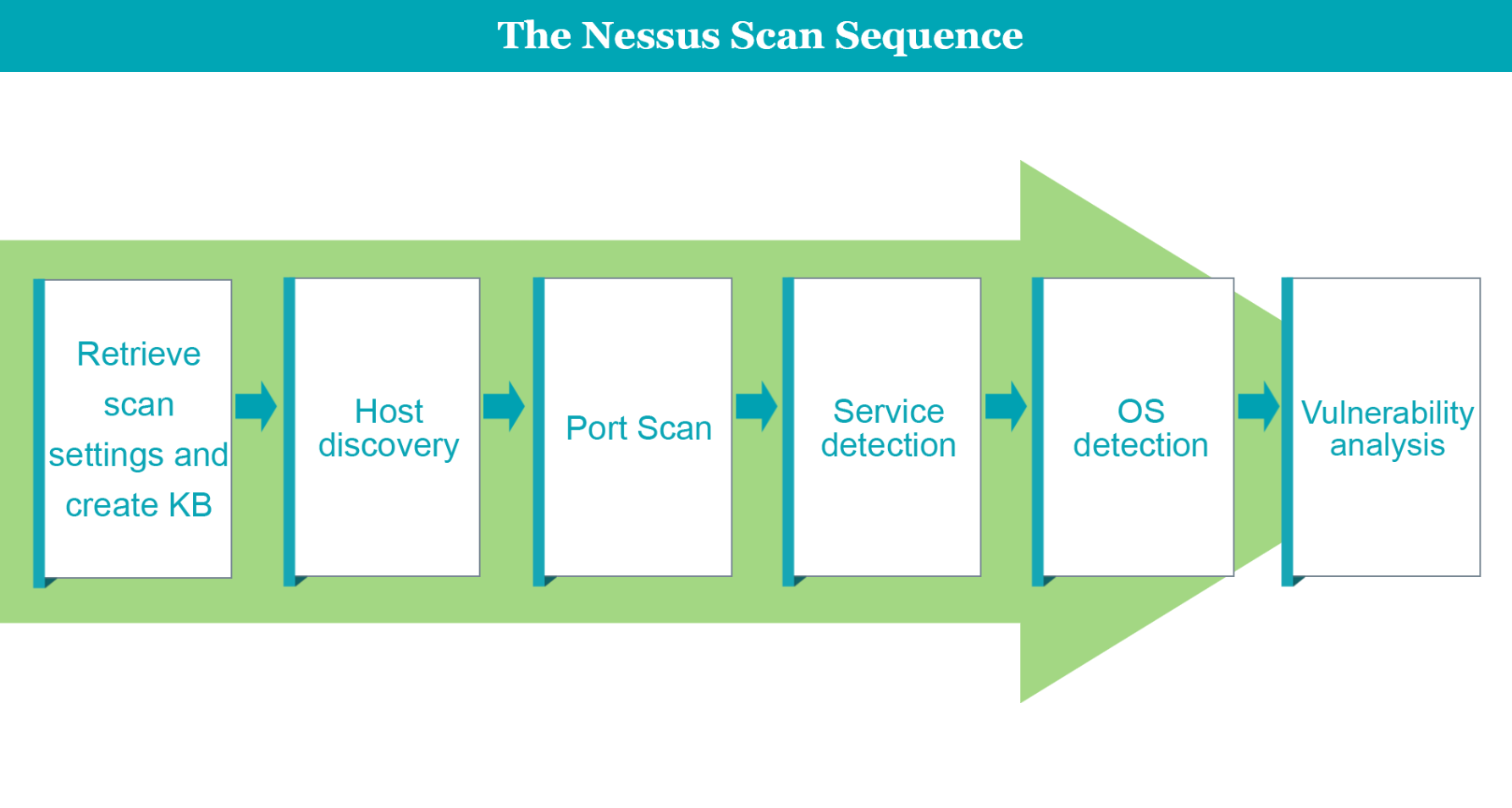
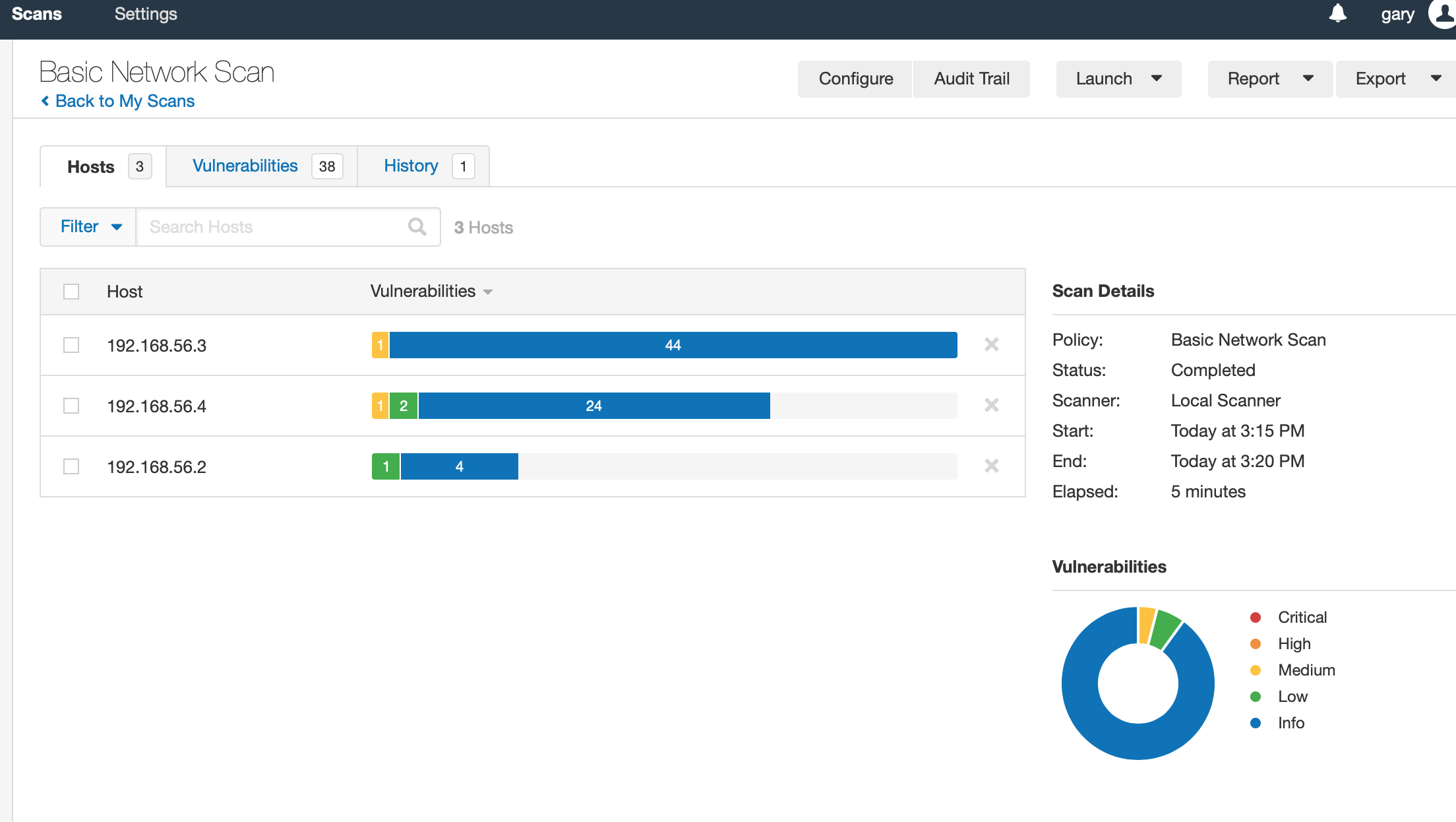
The security analyst carefully reviews the report, prioritizing vulnerabilities based on their severity and potential impact on the organization's security posture. The analyst identifies critical vulnerabilities that require immediate attention and devises a remediation plan accordingly.
Using the information provided in the NESSUS report, the analyst collaborates with the relevant teams to remediate the identified vulnerabilities. This involves implementing security patches, applying configuration changes, updating software versions, or making necessary adjustments to network infrastructure.
Throughout the remediation process, NESSUS continues to play an active role. The analyst leverages the platform's capabilities to validate the effectiveness of the applied remediation measures. By re-scanning the previously vulnerable assets, the analyst ensures that the vulnerabilities have been successfully mitigated and that the security posture has improved.
In the event that some vulnerabilities persist or new ones are discovered during the remediation process, the analyst utilizes NESSUS's reporting and tracking features to document the ongoing status of each vulnerability. This information is crucial for tracking progress, maintaining an audit trail, and ensuring that all vulnerabilities are addressed effectively.
Once all identified vulnerabilities have been remediated, the security analyst generates a final report that highlights the successful resolution of vulnerabilities and the improved security posture of the organization. This report serves as evidence of the proactive measures taken to mitigate risks and provides valuable insights for future vulnerability management strategies. Nessus provides predefined formatted report templates for presenting the results of a vulnerability scan conducted using Nessus. They includes sections such as executive summary, vulnerability details, risk assessment, and remediation recommendations. These templates help standardize the reporting process and ensure consistent and clear communication of the scan findings to stakeholders.

By following this high-level walkthrough, security analysts can effectively utilize NESSUS to conduct vulnerability scans, identify weaknesses, and drive the necessary remediation actions. NESSUS's active scanning capabilities, comprehensive reporting, and continuous monitoring features empower organizations to strengthen their security defenses and reduce the potential impact of cyber threats.
10. Consclusions
Nessus is a powerful tool for cybersecurity professionals, offering a range of benefits. The platform continually evolves to meet the challenges of the ever-changing threat landscape. Nessus helps organizations identify and address potential weaknesses in their systems and networks, enabling proactive risk management and an enhanced security posture. The platform actively integrates with emerging technologies and frameworks, including cloud platforms, IoT devices, and containerization technologies. By embracing these advancements, organizations can ensure that their security measures remain robust and adaptable.
