
AWS - SAA C03

Udemy - Ultimate AWS Certified Solutions Architect Associate SAA-C03 - Stephane Maarek
Study Schedule
| Section | Title | Time (min) | Week | Dates |
|---|---|---|---|---|
| 1 | Intro | 13 | Week 1 | 18-24 June |
| 2 | code/slide DL | 1 | ||
| 3 | Get started | 14 | ||
| 4 | IAM/CLI | 54 | ||
| 5 | EC2 Fundamentals | 40 | ||
| 6 | SAA level | 33 | ||
| 7 | EC2 Instance Storage | 58 | ||
| 8 | High Availability/scalability; ELB/ASG | 32 | ||
| 9 | RDS/Aurora/ElasitCashe | 68 | Week 2 | 25 June - 1 July |
| 10 | Route 53 | 88 | ||
| 11 | Classic Solutions Architect Discussion | 45 | ||
| 12 | S3 intro | 47 | ||
| 13 | S3 Advanced | 26 | Week 3 | 2-8 July |
| 14 | S3 Security | 52 | ||
| 15 | Cloudfront/Global Accelerator | 35 | ||
| 16 | AWS Storage Extras | 49 | ||
| 17 | Decoupling Applications (SQS, SNS, Kinesis, Active MQ) | 92 | ||
| 18 | Containters (ECS, Fargate, ECR and EKS) | 51 | Week 4 | 9-15 July |
| 19 | Serverless Overview | 76 | ||
| 20 | Serverless Solutions Discussions | 16 | ||
| 21 | Databases | 26 | ||
| 22 | Data Analytics | 50 | ||
| 23 | Machine Learning | 27 | ||
| 24 | Monitoring/Audit (CloudWatch, CloudTrail & Config) | 73 | Week 5 | 16-22 July |
| 25 | IAM advanced | 48 | ||
| 26 | Security/Encryption (KMS, SSM, Parameter Store, CloudHSM, Chield, WAF) | 92 | ||
| 27 | Networking VPC | 158 | Week 6 | 23-29 July |
| 28 | Disaster Recovery/Migrations | 41 | ||
| 29 | More Solutions Architectures | 28 | ||
| 30 | Other Services | 35 | ||
| 31 | White papers architectures | 15 | ||
| 32 | Prepare for exam/Practice Exam | 16 | ||
| 33 | Congrats | 3 | ||
| Pracitce Tests | Tests 1-6 in Udemy; 1 per day | Week 7 | 30 July - 5 August | |
| Review Practice Tests | Week 8 | 6-12 August | ||
| TEST DATE | FINISH LINE | 14 August |
NOTES : AWS Certified Solutions Architect (SAA-C03)
Section 1 - Intro
Section 2 - Code/slide DL
Section 3 - Getting Started
Section 4 - IAM & AWS CLI
Summary -
- Don't use root account except for account setup
- Assign users to groups, assign permissions to groups
- Use MFA (Multi-Factor Authentication)
- Create and use roles for giving permissions
- Use access keys for programmatic access (CLI/SDK)
- Audit permissions using IAM Credentials Report and IAM Access Advisor
IAM: Users & Groups
- Global Service
- Root account created by default; shouldn't be used or shared
- Users - people, can be grouped
- Groups - contain only users, NOT other groups
- Users don't have to belong to a group and can belong to multiple groups
IAM Policies Structure (JSON)
- Sid
- Effect - allow/deny
- Principal - account/user role to which the policy is applied
- Action - list of actions this policy allows or denies
- Resource - list of resources to which the actions are applied
- Condition
Security Groups - EC2 "firewalls"
- Can be attached to multiple instances
- Locked to a region/VPC combo
- Good to maintain one group for SSH access
- All inbound blocked by default
Multi-Factor Authentication (MFA)
- Virtual MFA device
- Google Authenticator (phone only)
- Authy (multi-device)
- Hardware key fob; provided by Gemalto
- Hardware key fob for AWS GovCloud (US); provided by SurePassID
- U2F Security key
User access to AWS (3 options)
- AWS Management Console
- Open source
- Direct access to public APIs
- AWS Command Line Interface (CLI)
- Directly access public APIs
- Develop scripts to manage resources
- Open source (github.com/aws/aws-cli)
- AWS Software Development Kit (SDK)
- Supports JavaScript, Python, PHP, .NET, Ruby, Java, Go, Node.js
- Mobile Devices (Android, iOS)
- IoT devices (embedded C, Arduino, etc.)
Security Tools
- IAM Credentials Report
- Report lists all user accounts and status of credentials
- IAM Access Advisor
- Show service permissions granted to a user when last accessed
- Used to revise policies
Section 5 - EC2 Fundamentals
Bootstrapping - launching command when machines starts, script runs once at first start in ROOt user.
Instance types
EX: m5.2xlarge; m: instance lass, 5: generation, 2xlarge: size within instance class
Security Groups - Ec2 "firewalls"
- Can be attached to multiple instances
- Locked to a region/VPC combo
- Good to maintain one group for SSH access
- All inbound blocked by default
- All outbound authorized by default
Ec2 types
- on demand
- pay for what you use, recommended for short-term and uninterrupted workloads
- Reserved
- Save $$ over on demand (72%)
- Period 1 or 3 years
- Regional or zonal
- Savings Plan
- Discount for long term usage
- Locked to a specific instance family and Region
- Spot
- Discount over on demand (90%)
- Most Cost Efficient
- NOT SUITABLE FOR CRITICAL JOBS OR DATABASES
- Dedicated Hosts
- Physical server fully dedicated to your use.
- Addresses compliance requirements
- Most Expensive option
- Dedicated Instance
- Instances run on hardware that's dedicated to you
- May share hardware with other instances in the same account
- No control over instance placement
Example M4.Large - us-east-1
| Price Type | Price Per hour |
| On demand | 0.10 |
| Spot | 0.038 |
| Reserved 1 year | 0.062 (no upfront) 0.058 (all upfront) |
| Reserved 3 year | 0.043 (no upfront) 0.037 (all upfront) |
| Ec2 Savings Plan 1 year | 0.062 (no upfront) 0.058 (all upfront) |
| Reserved Convertible 1 year | 0.071 (no upfront) 0.66 (all upfront) |
| Dedicated host | on-demand pricing |
| Dedicated host reservation | Up to 70% off |
| Capacity Reservations | On-Demand pricing |
- Target capacity with price constraints
Section 6 - EC2 Solutions
Private vs Public IP (by default EC2 comes with private IP and Public IP)
- Public IP - can identify the machine on the World Wide Web; unique across the entire web
- If the instance is restarted, the public IP changes
- Private IP - only identifies the machine on the private network; connects with NAT and Gateway (proxy)
Elastic IPs
- Public IPv4 you own as long as you don't delete it
- Can attach it to one instance at a time
- Only 5 in the account (unless you ask AWS to increase)
- Avoid use; reflects poor design, instead use a random public IP and register a DNS name to that IP
- Alternatively, you can use a load balancer in place of a public IP
Placement Group
- Cluster
- Low latency
- Single AZ
- Pro - great bandwidth (10Gbps)
- Con - if rack fails, all instances fail simultaneously
- Use case - Big Data jobs completed fast
Spread
- Max 7 per AZ
- Spreads instances across underlying hardware
- Pros - can spread across AZ, reduce failure, EC2 instances on different physical hardware
- Cons - limit 7 instances per AZ group
- Use Case - Critical Apps that need maximum availability
Partition
- Spread instances across many different partitions (on different sets of racks) within an AZ
Elastic Network Interfaces (ENI)
- Logical component in a VPC, represents a virtual network card
- Can be created independently and attached on the fly to EC2 instances
- Bound to a specific AZ
EC2 Hibernate
- Not supported on bare metal instances
- Available for on-demand, reserved, and spot instances
- No more than 60 days
- Preserves RAM (less than 150 GB)
- Boots faster
- Root EBS volume must be encrypted
- Use cases - long-running processing, save RAM state, services that take time to initialize
Section 7 - EC2 Instance Storage
Elastic Block Store (EBS) Volumes
- Attached to instances as they run
- Persist after the instance is terminated
- 1 instance at a time
- Bound to one Availability Zone (AZ)
- Acts like a network drive, not a physical drive
- Can be attached, detached, and reattached to another instance
- Must provision capacity in advance
- Delete on Termination is the default behavior for the root EBS volume, but not for other volumes
EBS Snapshot
- Not necessary to detach instances, but recommended
- A copy of the snapshot is stored across AZs
- Archive tier is 75% cheaper
- Takes 1-3 days to recover from a snapshot
- Recycle bin is available for 1 day to 1 year
- Fast Snapshot Restore (FSR) is very expensive
Section 8 - High Availability/Scalability (ELB/ASG)
Amazon Machine Image (AMI)
- Built for specific regions
- Faster boot
- Can be customized
- Can be public, created by yourself, or purchased from the marketplace
EBS Volume Types
< td>-| Volume Type | Size | IOPS/PIOPS | Throughput (MiB/s) | Notes | Use Case |
|---|---|---|---|---|---|
| Gp2 (SSD) | 1 GB - 16 TB | 3 IOPS per GB, 16000 max | - | Cost-effective, low-latency | Low-latency interactive apps, development and test environments |
| Gp3 (SSD) | 1 GB - 16 TB | 3000 - 16000 | 125 - 1000 | IOPS and throughput can be changed independently | |
| Io1 (SSD) | 4 GB - 16 TB | 3000 PIOPS bursts | - | For critical business apps with sustained PIOPS or 16K+ IOPS | Workloads that require sustained IOPS |
| Io2 (SSD) | 4 GB - 16 TB | 32000 PIOPS max, 64000 PIOPS max (Nitro) | - | For critical business apps with sustained IOPS or 16K+ PIOPS | Has more durability and PIOPS per GB than Io1 at the same cost |
| Io2 (SSD) Block Express | 4 GB - 64 TB | 256000 PIOPS max | - | Sub-millisecond latency, supports EBS Multi-Attach | Workloads requiring sub-millisecond latency |
| ST1 (HDD) | 125 GB - 16 TB | - | - | Low-cost HDD for frequently accessed, throughput-intensive workloads | Data warehouse, log processing |
| SC1 (HDD) | 125 GB - 16 TB | - | - | Lowest-cost HDD, less frequently accessed | Infrequently accessed workloads |
EBS Multi-Attach
- Allows attaching multiple EC2 instances in the same AZ
- Maximum of 16 EC2 instances
- Requires a file system that is cluster-aware
EBS Encryption
- Encrypted at rest, in transit between instances, snapshots, and volumes created from snapshots
- Handled transparently without user involvement
- Uses Key Management Service (KMS) with AES-256 encryption
- To encrypt an unencrypted EBS volume, create a snapshot, encrypt the snapshot, create a new EBS volume from the encrypted snapshot, and attach it to the original instance
Amazon Elastic File System (EFS)
- Network file system
- Can be attached to many EC2 instances in multiple AZs
- More expensive (3 times the cost of GP2)
- Does not require provisioning size at creation; it's elastic
- Uses NFSv4.1 protocol
- Uses security groups to control access
- Only compatible with Linux
Section 9 - RDS/Aurora
RDS
- RDS is a managed service
- You CANNOT SSH into your instances
Storage Auto Scaling
- Less than 105 GB of storage is free
- Use case: Unpredictable workloads
Read Replicas
- Up to 15 replicas
- Within AZ, cross AZ, or cross region
- Replication is asynchronous, so reads are eventually consistent
- Use cases: Production databases with normal load, reporting applications for analytics
- If read replicas cross region, there is a fee. Within the same region, it's free
RDS Multi AZ (Disaster Recovery)
- Single to multi AZ migration with no downtime
- Snapshot is taken, and a new DB is restored from the snapshot
- RS Custom
Amazon Aurora
- Proprietary to AWS
- Supports MySQL and PostgreSQL
- Cloud-optimized, provides 5 times better performance over MySQL and 3 times better performance over PostgreSQL
- Scales automatically in increments of 10 GB up to 128 TB
- Up to 15 replicas
- Costs 20% more than RDS but is more efficient
Features of Aurora
- Auto Scaling
- Custom Endpoints
- Serverless
- Multi-Master
- Global
- Machine Learning
Backups
- RDS
- Aurora
Restore Options
- RDS from S3
- Aurora from S3
Aurora Database Cloning
Security
- RDS
- Aurora
RDS Proxy
ElastiCache
- DB cache
- User Session Store
- Redis vs Memcached
- Cache Security
- Patterns
- Redis Use Case
Section 10 - Route 53
Google.com = 172.2.17.18.36
Domain:
restirar
DNS Records:
Zone file
Name server
Top Level Domain (TLD):
.com, .gov, .gov
Second Level Domain (SLD):
amazon.com
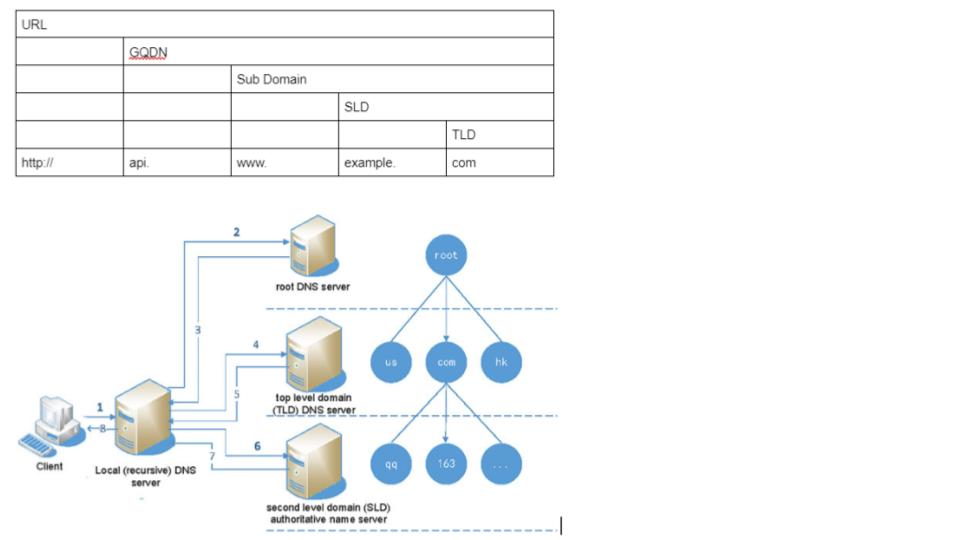
| Route 53 - fully managed Authoritative DNS |
|---|
| Authoritative = customer can update the DNS records |
| Also a domain registrar |
| THE ONLY AWS SERVICE WHICH PROVIDES 100% AVAILABILITY SLA |
| Route 53 - Records |
| How you want to route traffic for a domain |
| Each record contains: |
| Domain/subdomain Name: example.com |
| Record type: A / AAAA |
| Value: 12.34.56.78 |
| Routing Policy: route 53 responds to queries |
| TTL: amount of time the record cached at DNS resolvers |
| Supports the following DNS record types: |
| MUST KNOW - A / AAAA / CNAME / NS |
| Advanced - CAA / DS / MX / NAPTR / PTE / SOA / TXT / SPF / SRV |
| Route 53 - Record Types |
| Record Type | Description |
|---|---|
| A | Maps hostname to IPv4 |
| AAAA | Maps hostname to IPv6 |
| CNAME | Maps hostname to another Hostname Target domain must have an A/AAAA record. Can't be created for the top node of a DNS namespace (Zone Apex) |
| NS | Name servers for hosted zones Controls how traffic is routed for the domain |
Route 53 - Hosted Zones
Container for records that define how to route traffic to a domain and its subdomains
Public - contains records that specify how to route traffic on the internet (public domain names)
Private - contains records that specify how to route traffic within one or more VPCs (private domain names)
Cost $0.50 per month per hosted zone
Route 53 Records TTL (Time to Live)
High TTL (e.g., 24 hours)
Low TTL (e.g., 60 seconds)
NOTE: TTL is mandatory for each DNS record except for ALIAS RECORDS
CNAME vs Alias
AWS resources expose an AWS hostname (e.g., load balancer, CloudFront)
CNAME
- Points a hostname to any other hostname
- ONLY FOR NON ROOT DOMAINS
Alias
- Points a hostname to an AWS resource
- Works for ROOT DOMAIN and NON ROOT DOMAIN
Route 53 - Alias Records
Maps a hostname to an AWS resource
An extension to DNS functionality
Automatically recognizes changes in the resource’s IP
Unlike CNAME, it can be used for the top node and DNS namespace (Zone Apex)
Always of type A/AAAA for AWS resources (IPv4/IPv6)
Can NOT set the TTL
Route 53 - Alias Records Targets
NOTE: You can NOT set an ALIAS record for an EC2 DNS name
Routing Policies
Defines how Route 53 responds to DNS queries
Don't get confused by "routing" - it's not the same as a load balancer. DNS does NOT ROUTE TRAFFIC, it only responds to the DNS query
Supports the following routing policies:
- Simple: Typically to a single resource
- Weighted: Controls the % of requests that go to a specific resource
- Failover: Redirect to the resources with the least latency close to you
- Latency Based: Based on traffic between users and AWS Region
- Geolocation: Multi-value-answer
- Geoproximity: Using Route 53 Flow feature
Route 53 - Health Checks
HTTP health checks are ONLY for PUBLIC RESOURCES
Health check => Automated DNS Failover
Health checks that monitor:
- Endpoint (applications, servers, etc.)
- Other health checks (calculated health checks)
- CloudWatch Alarms (full control, e.g., throttles DynamoDB alarms on RDS)
Health checks are integrated with CloudWatch metrics
Health Checks - Monitor an Endpoint
About 15 Global health checkers
Healthy / Unhealthy threshold - 3 default
Intervals - 30 sec (can set to 10 at a higher cost)
Supported protocols: HTTP, HTTPs, TCP
If >18% of health checkers report the endpoint is healthy, Route 53 considers it healthy, otherwise, it is unhealthy
Ability to choose which locations you want Route 53 to use
Health checks pass only when the endpoint responds with 2xx and 3xx status codes
Can be set up to pass/fail based on the text in the first 5120 bytes of the response
Configure your router/firewall to allow incoming requests from Route 53 health checker
Health Checks - Calculated Health Checks
Combine results of multiple health checks into a single health check
You can use OR, AND, or NOT
Can monitor up to 256 Child Health checks
Specify how many of the health checks need to pass to make the parent pass
Usage: Perform maintenance on your website without causing all health checks to fail
Health Checks - Private Hosted Zones
Route 53 health checkers are outside the VPC
Can't access private endpoints
Can create CloudWatch metric and associate a CloudWatch alarm, then create a health check that checks the alarm itself
Routing Policies
Failover (Active-Passive):
Geolocation:
Geoproximity:
IP-based routing:
Multi-value:
Domain Registrar vs DNS Service
GoDaddy as Registrar and Route 53 as DNS Service:
3rd Party Registrar with Amazon Route 53